Last night we experienced high traffic on several ESXi servers that we manage on our network.
Most of them have ESXi 4.1 installed but this also affected ESXi 4.0.
Monitoring the network we saw that the traffic generated was UDP and not TCP thus bypassing our TCP QoS filters and alerts. The traffic was eventually originated from the ESX host itself and not VM’s running on each host.
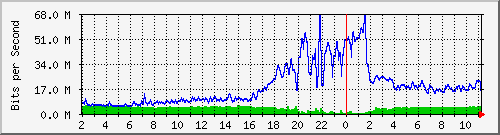
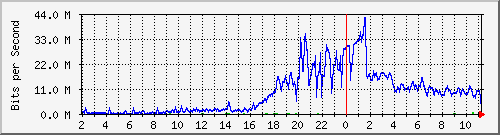
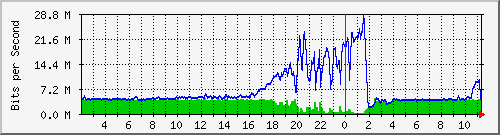
Below a graph of the uplink of the Vlan running 4 of the affected ESXi’s.
We noticed that 2 switches where affected, having unusual traffic but the amount of bandwidth each server used was very stable (approximately 10Mbps) and we focused on the Hypervisors.
Running tcpdump on the ESXi’s we noticed a high volume of NTP packets going out. After we disabled the NTP service on the ESX hosts, the traffic went back down to normal.
The attack is described here (even if it’s for a FreeBSD)