Today we received a rather interesting phishing email for iTune accounts and AppleID.
Just for the fun of it and since the email itself seemed “clean enough” to pass through even some suspicious users, we decided that we would follow it and create a post with what you’ll see and what you should notice in order not to become a victim of this (or possibly other well designed) phishing campaign.
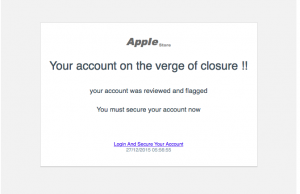
The email that came in looked rather simple. It contained no obvious mistakes, it does not match completely with the styling of Apple but then again, it’s clean and Apple does change from time to time their transactional email design. It did though pass through 2 different antispam systems (barracuda, 365 clutter) and also skipped the junk mechanism of the mail client (Outlook 2016).
If you are careful and suspicious for phishing emails, hovering the mouse over the link would certainly draw your attention, as would the address bar URL during the rest of the procedure. And in fact, this is one of the first and key ways to protect yourself from such attacks.
Usually, the use of a compromised web site is used to serve some hidden pages which will gather the information collected by the custom created forms.
This kind of attack, does not raise any attention to the website owner or the hosting company as is usually not generating much traffic (if the botnet is properly handled) and the hackers will be able to collect several data from batches of emails they will send.
It is extremely rare that the actual website claiming to send the email is the one compromised (especially when we are talking about big corporations provided services and online accounts but this is the case also for smaller companies and eshop owners).
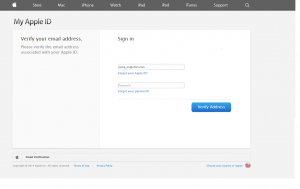
The link redirected us to this page:
Again a clean design, this time much closer to Apple’s design but once again if you are careful you will notice that the top menu is not operational, the copyright is from 2014 and of course the browser URL has nothing to do with Apple’s domains.
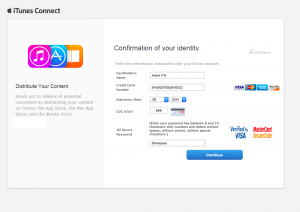
Once you submit your AppleID and password, you are taken to the following page, requesting your Credit Card details:
At this point, if you have submitted this information, you can consider yourself compromised. You should change your AppleID password and cancel your credit card.
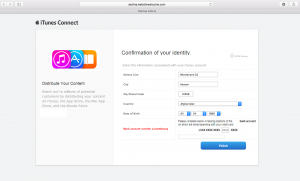
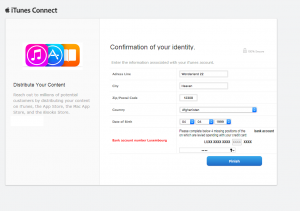
The next 2 steps, request your Address & Bank account details:
Finally, you are taken to Apple’s site but the damage has already been made since all the information provided on the previous lists are now in the hands of the attackers. Apple.com’s EV certificate can be seen on the address bar after the completion of the last step of the phishing email:
The conclusion is that you must be very certain that the site you are redirected to through any transactional email (no matter how legit it looks) is actually a proper, signed and (in most cases) secure URL and don’t ever hesitate contacting the company from which you have received the email to personally verify it. Giving away your online account along with credit card, address and bank details information can get you into weeks of paperwork and loss of money, time and possibly some online data.